Identity Providers
Identity providers are services that authenticate users and manage their identity.
Identity providers (IdPs) are responsible for authenticating users and managing their identities. Therefore, in order for users to log in to your application, you'll need to configure at least one identity provider. By default, Wristband itself will be enabled as an identity provider; however, external identity providers can also be enabled to allow users to authenticate using an existing identity. In the following sections, we'll go over the different types of identity providers that Wristband supports.
Wristband Identity Provider
Wristband itself can be used as an IdP and is enabled by default when an application is first created. The Wristband IdP can be configured to allow users to authenticate using the following login identifier and login factor permutations:
Supported Login Identifier Permutations
- Email Only: Users must provide their email address to identify themselves.
- Email or Username: Users can provide their email address or username to identify themselves.
Supported Login Factor Permutations
- Password: Users will be required to enter a password to log in.
- Magic Link: After entering their email address, users will be sent an email containing a link to log in.
- Password or Magic Link: Users can log in using either a password or a magic link.
Multi-Factor Authentication (MFA)
Multi-factor authentication can be configured for the Wristband IdP using MFA policies. MFA policies can be configured at either the application level or the tenant level. MFA policies configured at the application level will affect all users under the application; whereas MFA policies configured at the tenant level will only affect users under that tenant. The following settings can be controlled through MFA policies:
- MFA Enrollment Requirements: If MFA enrollment is required, users must complete MFA setup before they can authenticate. The following Wristband flows will automatically prompt users to enroll (if they haven’t already) when MFA is marked as mandatory:
- User invite
- Password reset (if immediate login is enabled)
- Login
- Signup
- Enabled MFA Factors: Using MFA policies, you can configure which MFA factors are enabled. Currently, the following MFA factors are supported:
- TOTP: Users will need to enter a Time-based One-Time Password, generated by an authenticator application such as Google Authenticator or Authy. Currently, this factor must be enabled if MFA is required.
- Recovery Code: After a user completes MFA enrollment, they will be provided with a one-time code that they can use if they can't authenticate using their enrolled factor.
- Issuer: This setting can be used to change the issuer name that appears in authenticator apps when a user enrolls in the TOTP factor. If unspecified, this value defaults to the application's display name.
NoteMFA policies don't have any effect on users authenticating using an external identity provider. If MFA is required for users belonging to an external IdP, then the external IdP should be configured to enforce MFA enrollment.
External Identity Providers
Wristband also allows you to integrate with external IdPs, enabling users to authenticate with an existing identity. Wristband groups external IdPs into two categories:
- Social Identity Providers
- Enterprise Identity Providers
In the following sections, we'll take a closer look at the IdPs supported within each of these two categories.
Social Identity Providers
Social identity providers allow users to log in with their personal identities managed by popular cloud-based services. Typically, you'll use social logins for consumer-facing applications or product-led growth B2B applications where individuals can self-onboard. Below is a table showing all the social identity providers currently supported by Wristband:
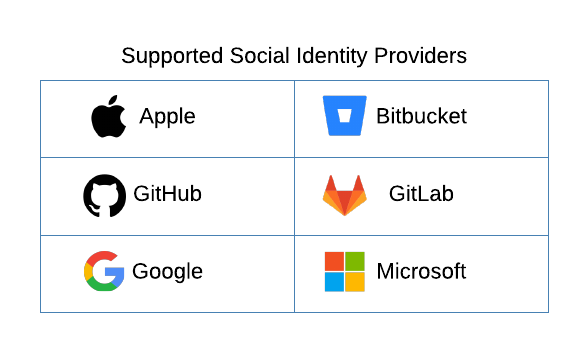
To learn more about how to configure social identity providers, please refer to the Configuring Social Identity Providers documentation.
Enterprise Identity Providers
An enterprise identity provider allows users to authenticate using credentials managed by an external organization, typically their employer. Enterprise IdPs are commonly used to enable Single Sign-On (SSO), allowing users to access multiple applications with a single, centrally managed identity. In B2B scenarios, enterprise IdPs are configured for customer organizations so their employees can securely access your application using their existing workplace credentials.
Enterprise identity providers are typically integrated using either the SAML 2.0 or OIDC protocol. The table below lists the enterprise IdPs supported by Wristband and the protocols Wristband supports for each one.
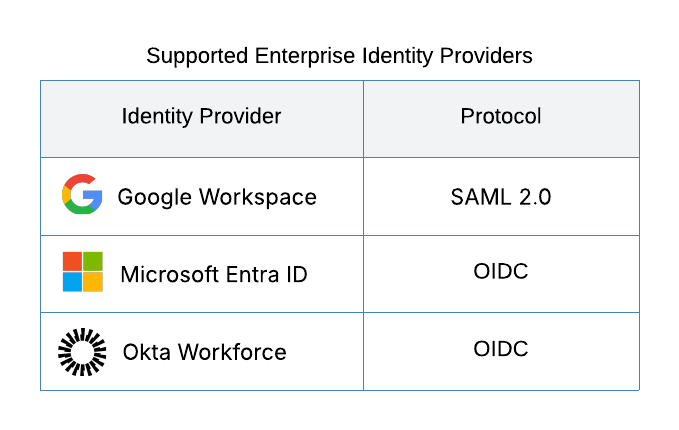
To learn more about how to configure enterprise identity providers, please refer to the Configuring Enterprise Identity Providers documentation.
Custom Identity Providers
If an organization is using an identity provider that is not supported out of the box by Wristband, you can still integrate with it by configuring a custom identity provider. Currently, custom identity providers can integrate with enterprise IdPs using the following protocols:
- SAML 2.0
NoteEnterprise identity providers can only be configured at the tenant level, as they must be tied to an external organization. One exception is that they cannot be created for Global Tenants, since they are intended to contain users that aren't associated with an organization.
Updated 5 months ago