Role Mapping
In enterprise Single Sign-On (SSO), "role mapping" refers to the process of associating user roles within an organization's identity provider to specific permissions or access levels in another application or system
In enterprise Single Sign-On (SSO), "role mapping" refers to the process of associating user roles within an organization's identity provider to specific permissions or access levels in another application or system. This helps define and control what actions or resources a user with a particular role can access once they have authenticated via SSO. Wristband allows you to map the roles assigned to a user in an organization's identity provider with custom roles in your application. This ensures that users receive the appropriate level of access to your application based on their organizational roles.
Security Benefits of Role Mapping
In many organizations, either the IT team or a CISO mandates the implementation of role mapping for any SaaS apps used. Utilizing Wristband's role mapping capabilities helps maintain a consistent implementation across different applications by addressing the following aspects:
- Least Privilege Principle: Role mapping aligns with the principle of least privilege, where users are granted the minimum level of access required to perform their job functions. This minimizes the potential impact of security breaches, as compromised accounts have limited access.
- Efficient User Lifecycle Management: As users' roles change within the organization, role mapping facilitates seamless adjustments to their access levels. When an employee's responsibilities change, their role can be updated in the organization's identity provider, automatically adjusting their access permissions in your application accordingly.
- Audit Trails and Compliance: Role mapping provides a clear audit trail of user activities, as access is tied to specific roles. This aids in compliance efforts by allowing organizations to demonstrate that access controls align with regulatory requirements and internal policies.
- Centralized Control: By consolidating access management via role mapping, organizations gain centralized control over user permissions. This reduces the likelihood of inconsistent access control across your application and other applications they use.
How Role Mapping Works
When Just In Time (JIT) Provisioning is enabled for an enterprise external identity provider, Wristband streamlines the login process by dynamically assigning roles to users during authentication. Upon login, Wristband fetches the user's groups from the external identity provider and assigns corresponding Wristband roles. This instant role assignment guarantees users the right access permissions, enhancing the login experience and maintaining consistent access control.
Establishing Roles in the External Identity Provider
To enable role mapping for an external Identity Provider (IDP) in one of your Wristband tenants, start by configuring the IDP from its corresponding administration console. Assuming you've already established application integration within the provider for SSO login with Wristband, you need to create groups for the relevant organization.
For example, if a tenant wanted to use Microsoft Entra ID to perform SSO login with JIT provisioning and role mapping, you would establish a security group in the Azure admin console.
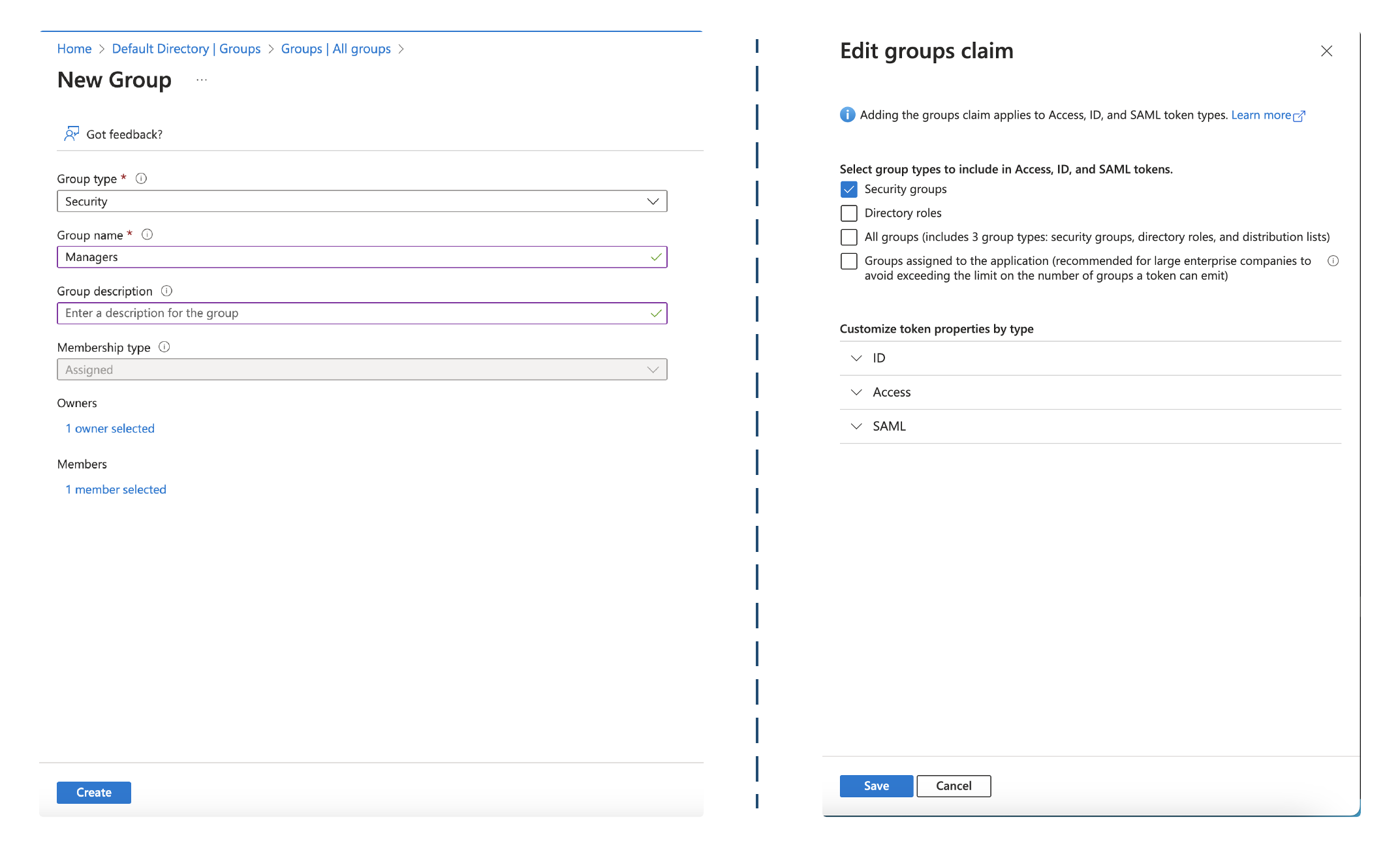
After all groups have been established, you must configure your SSO application in Entra to declare a groups optional claim so that group information is returned in the ID tokens. Wristband requires that claim to perform the mapping to roles for your application.
Location of GroupsEach external identity provider exposes group information differently, depending on their security protocol implementation. To understand how to set up roles in each supported external identity provider, refer to the IDP-specific tutorials.
Mapping Roles in Wristband
Setting up roles in the external identity provider is only a part of the process to enable role mapping. You also need to use the Wristband dashboard to associate groups with specific Wristband roles. Navigate to the Edit Enterprise External IDP Page.
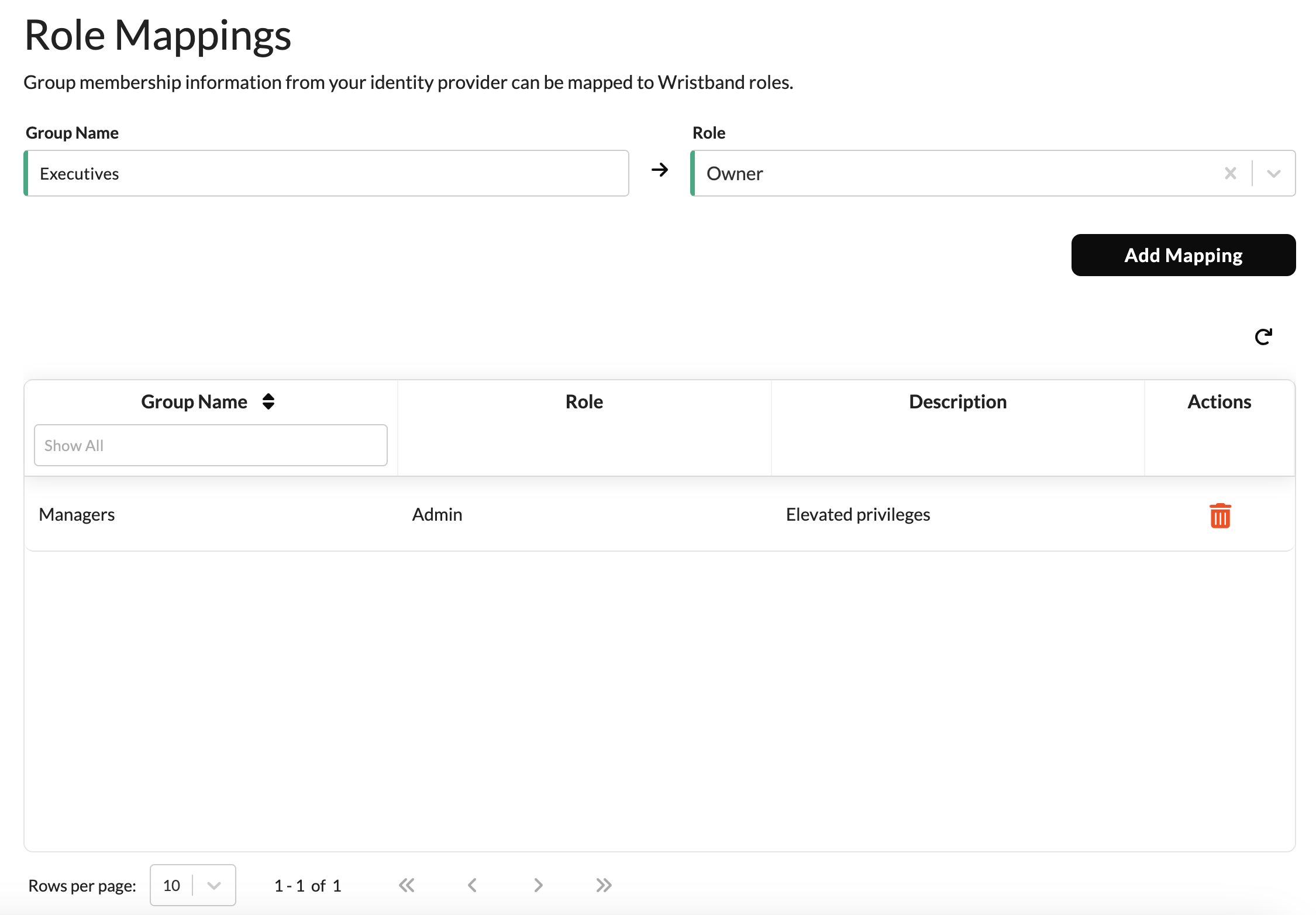
Here, you would map each group name to your desired Wristband role. It is possible to map a single group name to more than one Wristband role at a time.
Mapping LimitationsA single group from the external identity provider can be mapped to at most 5 Wristband roles. Each external identity provider can have at most 200 role mappings.
Role Assignment During JIT Provisioning
Enable JIT Provisioning for your enterprise external identity provider to implement role mapping. The role mappings created in Wristband will dynamically assign roles to users who get JIT provisioned based on the groups retrieved from the identity provider at the time of authentication. This process ensures that users receive the appropriate roles and access permissions in real-time, aligning with their current attributes or contextual information.
As an illustration, if you have included the roles claim in your authorization request to the Wristband Authorize Endpoint, after the successful completion of the JIT Provisioning login, the authenticated user would receive an access token. This token can be used to invoke the Wristband UserInfo Endpoint, and the ensuing response would display any mapped roles, exemplified as follows:
{
"sub": "y7ng4dlhcnfiddbz2tifv73ivu",
"tnt_id": "kh643sdf5ze6zcqb2e25dm5w6u",
"app_id": "m7k55onh6nbsjggayhubbef4eq",
"idp_name": "wristband",
"roles": [
{
"id": "xhmwelq5fjetfmugxtwdy5oziy",
"name": "app:yourapp:admin",
"displayName": "Admin"
}
]
}Default User Sync IDP Roles
Default roles enhance the efficiency of role mapping during JIT provisioning by providing predefined access permissions for users without explicit group or role assignments. You can implement a policy governing role assignments for users during JIT provisioning into your application. Following an SSO login with JIT provisioning, users are automatically assigned roles based on the specified default user sync IDP role assignment policy, configured through the Wristband dashboard.
Updated 5 months ago