Test Auth Middleware
Test that the auth middleware is verifying the session cookie for your Session Endpoint.
Tests not working?If you get stuck, contact us and our development team will work directly with you to get unblocked.
Now that you've added the auth middleware, let's check that the Session Endpoint is properly verifying the user's session cookie.
1. Verify Redirect to Login When Unauthenticated
When a user attempts to access a protected page in your application, the auth middleware should verify that the user has a valid session. If the session is invalid or doesn't exist, then your application should redirect the browser to your Login Endpoint, which in turn will redirect to Wristband's hosted login page.
Test Steps
- Open a browser and set up the browser's dev tools to actively monitor network requests. Also, ensure that network requests are configured to be preserved so you can examine them afterward.
- Make sure that you've logged out of your application so there's no existing session cookie stored in your browser.
- Navigate directly to a protected page within your application. For example,
http://localhost:3000/your-application-home-route. Because your user doesn't have an authenticated session, you should get redirected to Wristband's hosted login page.
Verification Checks
-
In your browser's developer tools, find the network request to your application's Session Endpoint. Verify in the network request that the response is 401.
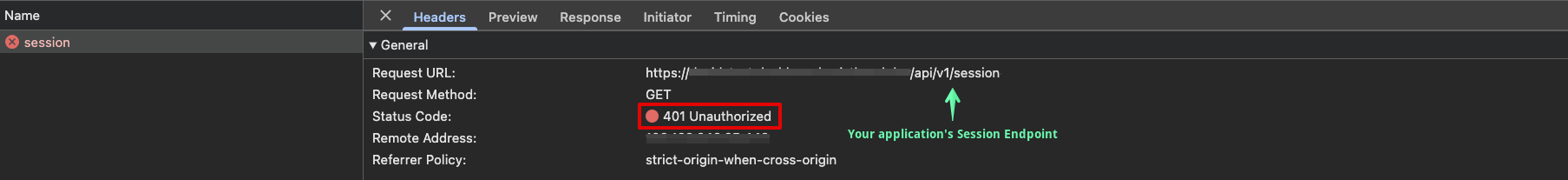
-
In the network request logs, verify that after receiving the 401 response, the browser is redirected to your application's Login Endpoint. Your application's Login Endpoint should then redirect to Wristband's authorize endpoint.
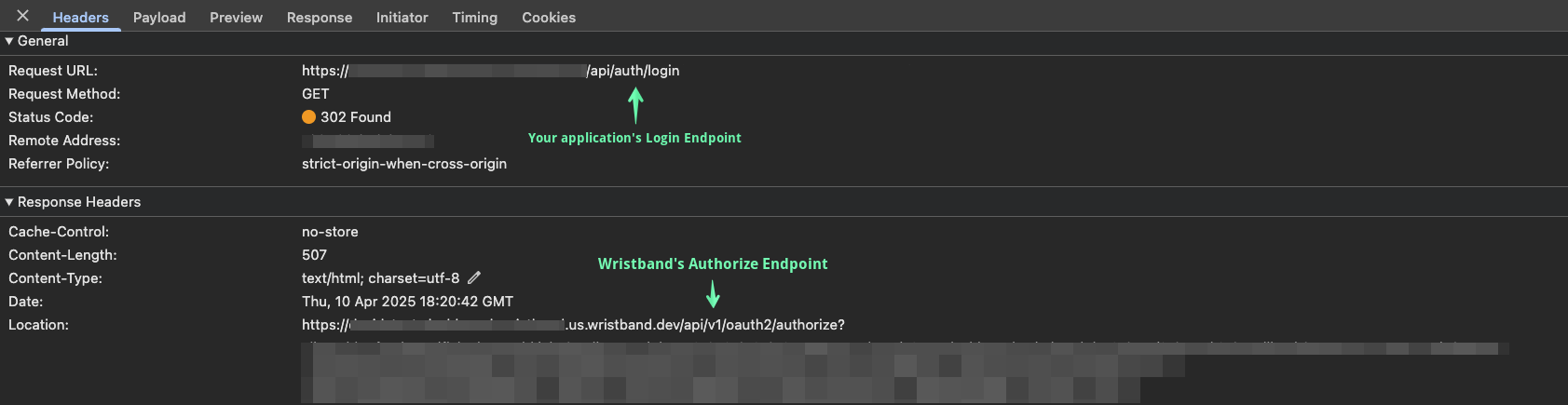
-
Verify that you land on Wristband's hosted login page.
2. Verify Successful Login
After landing on Wristband's hosted login page, complete the login flow to create a new authenticated session. Now that your user has an authenticated session, you should be able to navigate to your application's protected pages successfully.
Test Steps
- Ensure that your browser's dev tools are actively monitoring network requests. Also, confirm that network requests are configured to be preserved so you can examine them afterward.
- Complete the login flow for your user.
Verification Checks
-
Verify that after logging in, you are able to navigate to your application's protected pages successfully.
-
In your browser's developer tools, find the network request to your application's Session Endpoint. Because your user now has an authenticated session, the response from the session endpoint should be a 200.
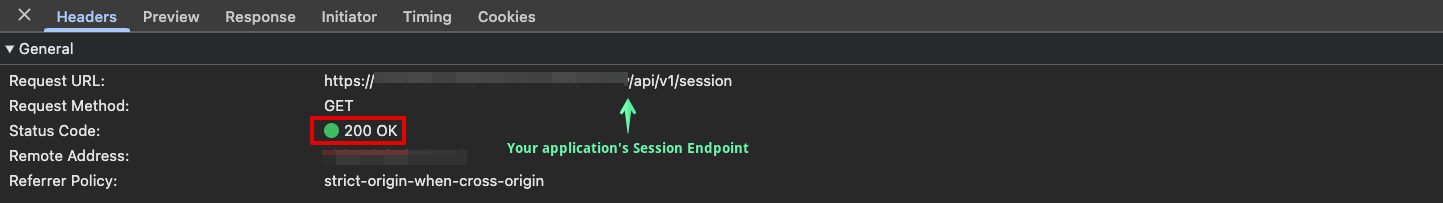
If the above tests succeed, then your auth middleware is working as expected! 🎉

Unauthorized access? Not in YOUR routes!
Updated 25 days ago
Next, we'll implement Cross Site Request Forgery (CSRF) in your backend to prevent misuse of the session cookie.