Login: Wristband Hosted-UI
Use Wristband’s hosted Login pages for a seamless multi-tenant auth experience out of the box.
All example flow diagrams below demonstrate a Backend Server OAuth2 Client type. The other client types can be inserted into the Login Workflow in a similar manner by following the examples and patterns laid out in the Integration Patterns documentation.
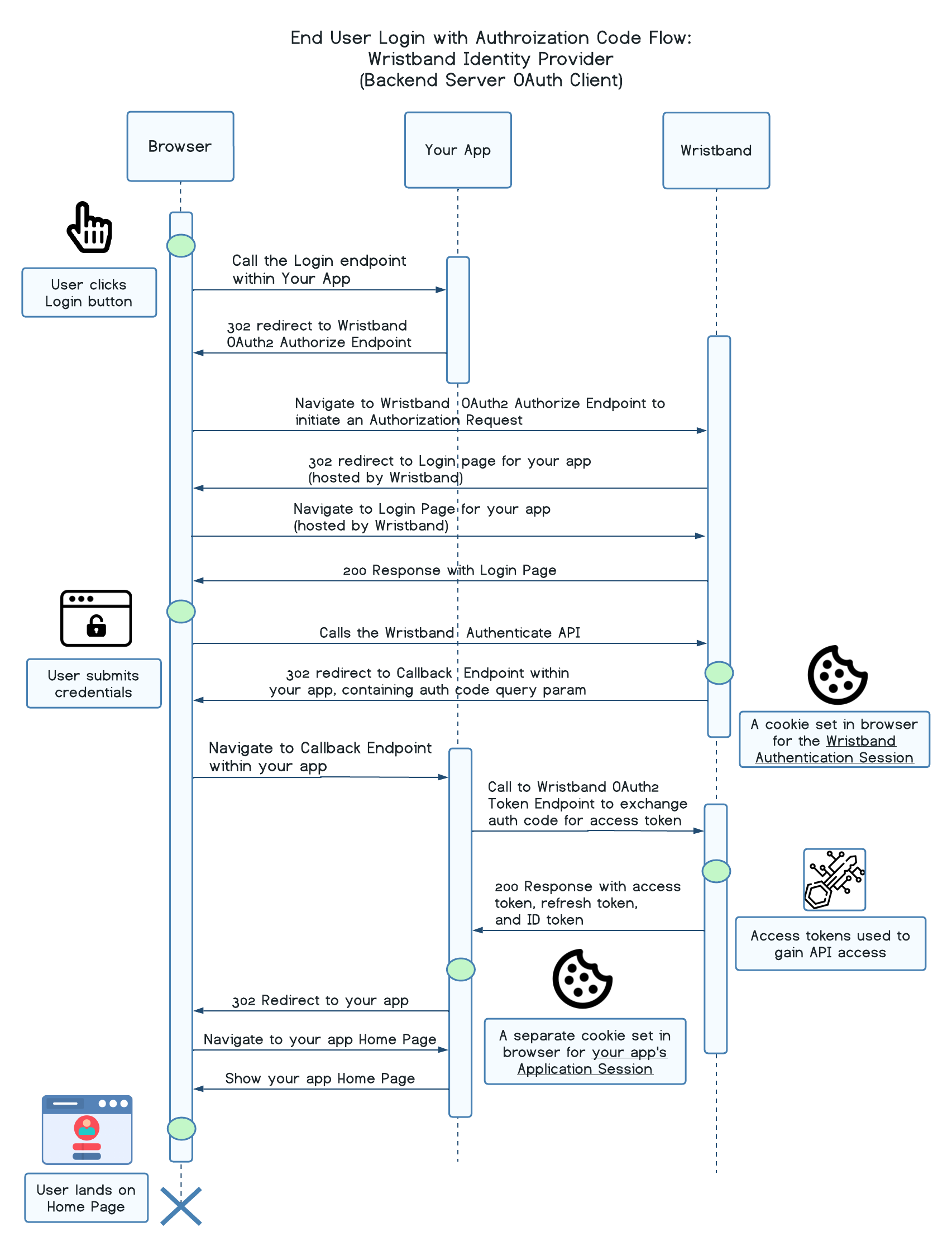
Wristband Identity Provider: Password Login
At a high level:
- The user clicks on the Login button either on your website or within your application.
- The user gets sent to the Login Endpoint implemented by your application's backend server.
- The backend server creates an Authorization Request and redirects the user to the Wristband Authorize Endpoint.
- Wristband validates and records the Authorization Request and then subsequently redirects the user to the Wristband-hosted Login page for your application.
- The user provides their credentials on the Login page to authenticate.
- Upon successful authentication, the Login Page will redirect to your application's Callback Endpoint with an authorization code.
- The Callback Endpoint will call the Wristband Token Endpoint in order to exchange the authorization code for an access token.
- The Callback Endpoint will establish an application session for the end user. The session contains the access token and refresh token (and optionally the ID token and/or any other useful user data). A session cookie is generated by the server.
- The Callback Endpoint redirects the user into your application's entry point of choice (e.g. the home page).
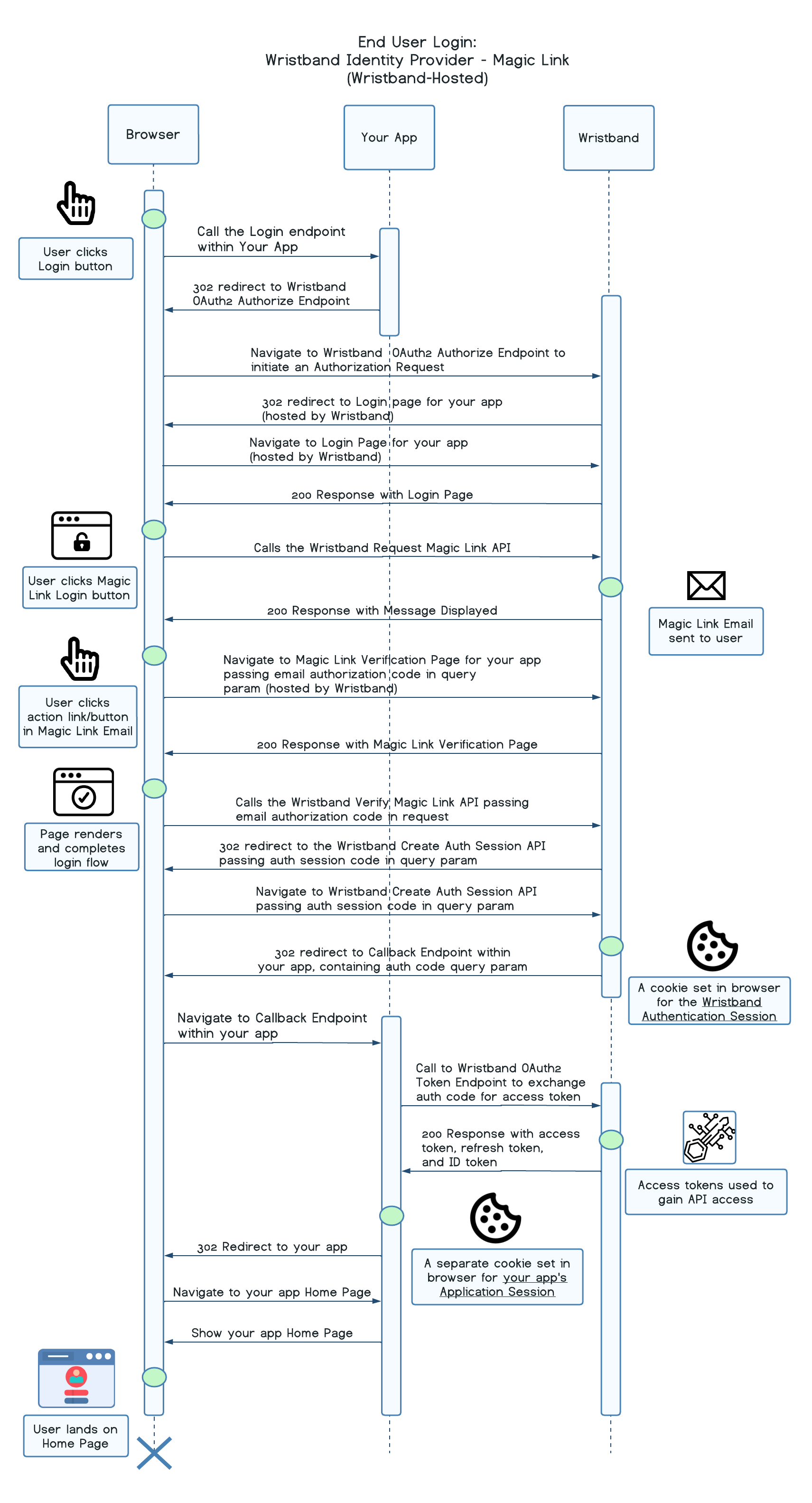
Wristband Identity Provider: Magic Link Login
The default login factor for the Wristband Identity Provider is Password Login, but you can opt to configure Magic Link Login instead. Additionally, you have the flexibility to enable both Password Login and Magic Link Login simultaneously. When both are active, the end user can choose the preferred method on the Login Page.
Magic Link Login operates by the end user entering their email address on the Login Page. Subsequently, Wristband dispatches a transactional email to that address, including a magic link. This link holds a one-time email authorization code, which, once clicked, authenticates the user with Wristband.
At a high level:
- The user clicks on the Login button either on your website or within your application.
- The user gets sent to the Login Endpoint implemented by your application.
- Your application creates an Authorization Request and redirects the user to the Wristband Authorize Endpoint.
- Wristband validates and records the Authorization Request and then subsequently redirects the user to the Wristband-hosted Login page for your application.
- The user clicks the Login button, which triggers a call to the Wristband Request Magic Link for Login API.
- The Login Page will show a message telling the user to check their inbox for a Magic Link Email.
- The user will click on the Magic Link within the email that was sent from Wristband.
- The user is sent to the Verify Magic Link Page, where a call to the Wristband Verify Magic Link API is triggered to authenticate the user.
- Upon successful authentication, the Login Page will redirect to your application's Callback Endpoint with an authorization code.
- The Callback Endpoint will call Wristband's Token Endpoint to exchange the authorization code for an access token.
- The Callback Endpoint will establish an application session for the end user. The session contains the access token and refresh token (and optionally the ID token and/or any other useful user data). A session cookie is generated by the server.
- The Callback Endpoint redirects the user into your application's entry point of choice (e.g., the home page).
External Identity Provider Login
External Identity Providers refer to any identity provider that is not Wristband. This includes both Social Login Providers and Enterprise Single Sign-On (SSO) Providers. Before you enable an External Identity Provider for your authentication method, you should refer to the setup instructions for your given identity provider.
Configuring Identity Providers Documentation:
External IDP Login Examples
The example diagrams below demonstrate External IDP Login using Google as the provider. From the point of view of Wristband, the flow is essentially the same when using other External Identity Providers as well.
At a high level:
- The user clicks on the Login button either on your website or within your application.
- The user gets sent to the Login Endpoint implemented by your application.
- Your application creates an Authorization Request and redirects the user to the Wristband Authorize Endpoint.
- Wristband validates and records the Authorization Request and then subsequently redirects the user to the Wristband-hosted Login page for your application.
- The user clicks the Login with Google button, which triggers a call to the Wristband External IDP Authorize Endpoint.
- Wristband redirects the user to Google's account login page.
- The user submits their Google credentials.
- Google redirects the user to the Wristband External IDP Callback Endpoint (which can be found in the Identity Providers section of the Wristband Dashboard for your given IDP), where Wristband creates an External IDP Authorization Code required for completing authentication.
- The user is sent to the Wristband-hosted External IDP Login Page -- along with the External IDP authorization code -- where a call to the Wristband Verify User for External IDP Login API is triggered to authenticate the user.
- Upon successful authentication, the Login Page will redirect to your application's Callback Endpoint with an authorization code.
- The Callback Endpoint will call Wristband's Token Endpoint to exchange the authorization code for an access token.
- The Callback Endpoint will establish an application session for the end user. The session contains the access token and refresh token (and optionally the ID token and/or any other useful user data). A session cookie is generated by the server.
- The Callback Endpoint redirects the user into your application's entry point of choice (e.g., the home page).

Enterprise SSO with JIT Provisioning
When Just In Time (JIT) Provisioning is enabled for an enterprise external identity provider, the login workflow changes after the user authenticates with the external IDP. Despite workflow policy configurations or other conditions, the SSO login workflow with JIT provisioning follows a common sequence up to a certain point. At a high level, this represents the shared portion of the sequence of events:

No Email Verification Required

Email Verification with One-Time Password

Email Verification with Asynchronous Email Confirmation

Updated 5 months ago